Начните с малого, сотрите все правила из Firewall.
1) Разрешите формард пакетов в системе между интерфейсами.
cat /proc/sys/net/ipv4/ip_forward - тут должна быть единичка (1).
2) 10.0.1.1 должен быть как GW 10.0.1.2 иначе трафик надо маскарадить через SNAT.
3) Добавьте правилось проброса порта
-A PREROUTING -i enp0s3 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80
4) Добавьте правило маскара, что бы маскарадить ответы от 10.0.1.2.
-A POSTROUTING -o enp0s3 -j MASQUERADE
Когда у Вас получится рабочий минимум, можете добавлять остальные правила.
П.С. Исходящий трафик (OUTPUT ) фильтруют параноики)
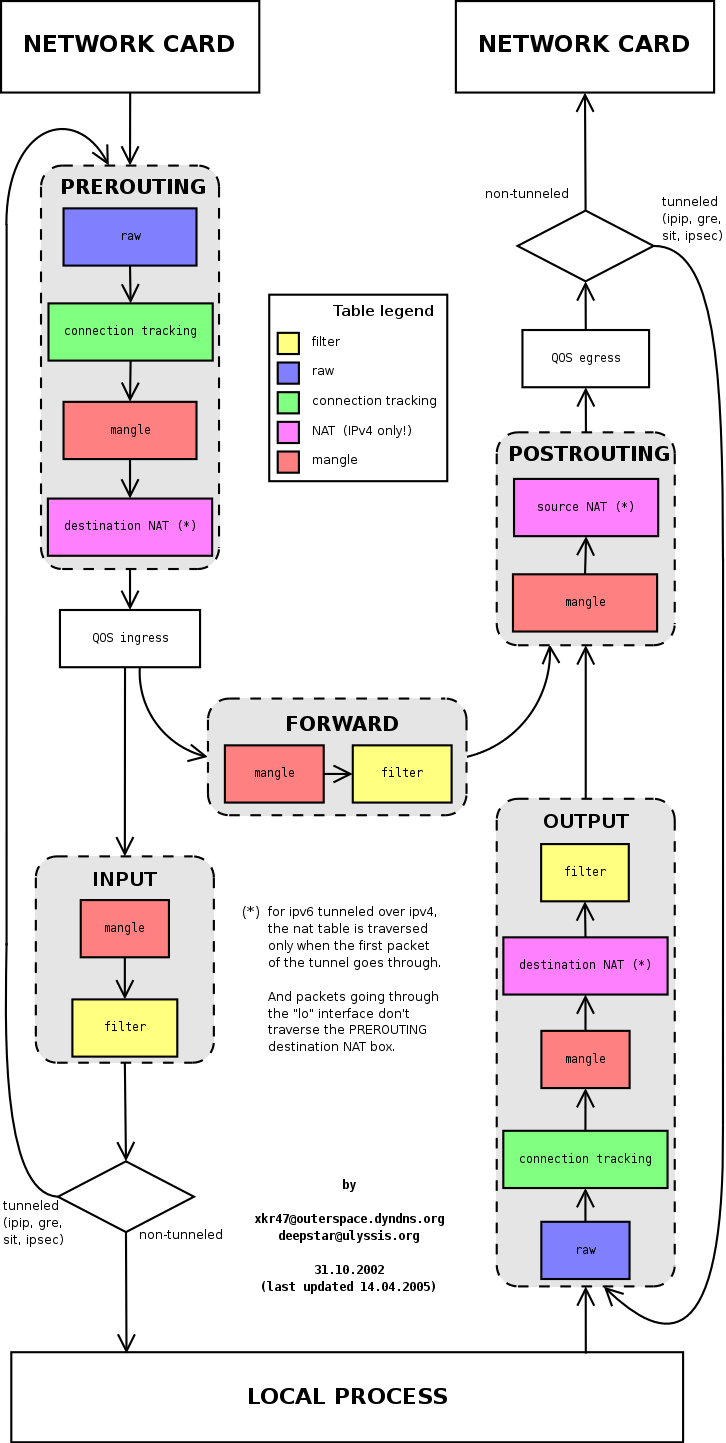
Хорошая картинка для понимания работы iptables