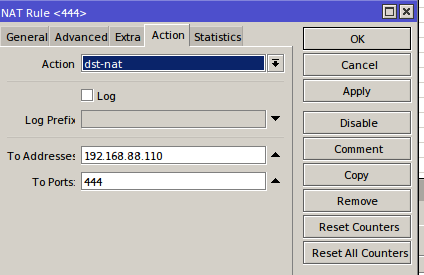
Ниже, рабочая конфигурация для firewall/NAT с открытыми портами для L2TP IPSec, веб-интерфейсом и пробросом 444 порта на ip 192.168.88.110
/ip firewall nat
add action=masquerade chain=srcnat comment="masquerade" ipsec-policy=out,none out-interface-list=WAN
add action=netmap chain=dstnat dst-port=444 in-interface=ether1 protocol=tcp to-addresses=192.168.88.110 to-ports=44
/ip firewall filter
add action=accept chain=input comment="ALLOW ESTABLISHED" connection-state=established
add action=accept chain=input comment="ALLOW RELATED" connection-state=related
add action=drop chain=input comment="DROP INVALID" connection-state=invalid
add action=accept chain=input comment="ALLOW ICMP" protocol=icmp
add action=accept chain=input comment="ALLOW WINBOX" dst-port=8291 protocol=tcp
add action=accept chain=input comment="ALLOW L2TP IPSEC" dst-port=500,1701,4500 in-interface=ether1 protocol=udp
add action=accept chain=forward comment="ALLOW L2TP IPSEC" protocol=ipsec-esp
add action=accept chain=input comment="ALLOW WEB-INTERFACE" dst-port=80 protocol=tcp
add action=drop chain=input comment="DROP ALL INPUT"
add action=accept chain=forward comment="ALLOW ESTABLISHED" connection-state=established
add action=accept chain=forward comment="ALLOW RELATED" connection-state=related
add action=drop chain=forward comment="DROP INVALID" connection-state=invalid
add action=accept chain=forward comment="ALLOW ICMP" protocol=icmp
add action=accept chain=forward comment="ALLOW REDIRECT TO RDP" dst-port=444 protocol=tcp
add action=accept chain=forward comment="ALLOW INTERNET FROM LOCAL" out-interface=ether1 src-address=192.168.88.0/24
add action=drop chain=forward comment="DROP ALL FORWARD"