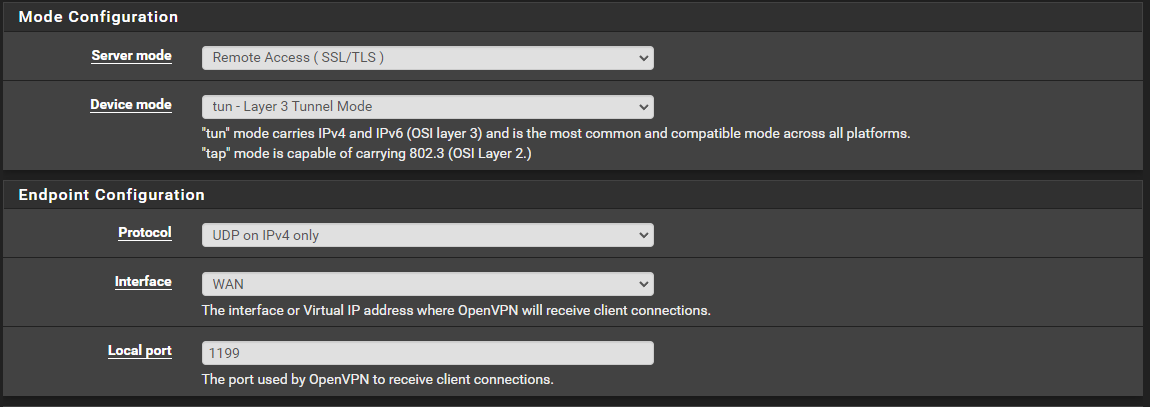
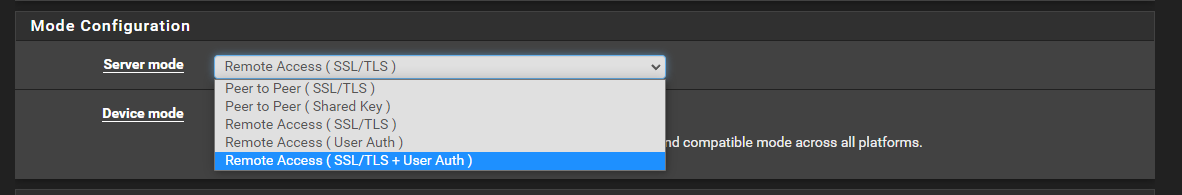
pfSense сбил с толку, VPN сервер Mode: Remote Access ( SSL/TLS ) отсутствие User Auth я предполагал что пользователя не нужно добавлять в pfSense.
1. добавляем пользователя в pfSense.
2. создаём сертификат для пользователя
3. создаём конфиг
dev tun
persist-tun
persist-key
ncp-disable
cipher none
auth none
tls-client
client
resolv-retry infinite
remote VPN.vitko-core.ru 1199 udp4
nobind
verify-x509-name "vpn.vitko-core.ru" name
remote-cert-tls server
explicit-exit-notify
<ca>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
-----END PRIVATE KEY-----
</key>
Wed Jul 13 11:40:25 2022 WARNING: cipher 'none' specified for --data-ciphers. This allows negotiation of NO encryption and tunnelled data WILL then be transmitted in clear text over the network! PLEASE DO RECONSIDER THIS SETTING!
Wed Jul 13 11:40:25 2022 OpenVPN 2.5.7 Windows-MSVC [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on May 27 2022
Wed Jul 13 11:40:25 2022 Windows version 10.0 (Windows 10 or greater) 64bit
Wed Jul 13 11:40:25 2022 library versions: OpenSSL 1.1.1o 3 May 2022, LZO 2.10
Wed Jul 13 11:40:26 2022 ******* WARNING *******: '--cipher none' was specified. This means NO encryption will be performed and tunnelled data WILL be transmitted in clear text over the network! PLEASE DO RECONSIDER THIS SETTING!
Wed Jul 13 11:40:26 2022 ******* WARNING *******: '--auth none' was specified. This means no authentication will be performed on received packets, meaning you CANNOT trust that the data received by the remote side have NOT been manipulated. PLEASE DO RECONSIDER THIS SETTING!
Wed Jul 13 11:40:26 2022 TCP/UDP: Preserving recently used remote address: [AF_INET]62.221.80.33:1199
Wed Jul 13 11:40:26 2022 UDPv4 link local (bound): [AF_INET][undef]:1194
Wed Jul 13 11:40:26 2022 UDPv4 link remote: [AF_INET]62.221.80.33:1199
Wed Jul 13 11:40:27 2022 [vpn.vitko-core.ru] Peer Connection Initiated with [AF_INET]62.221.80.33:1199
Wed Jul 13 11:40:27 2022 open_tun
Wed Jul 13 11:40:27 2022 tap-windows6 device [OpenVPN TAP-Windows6] opened
Wed Jul 13 11:40:27 2022 Set TAP-Windows TUN subnet mode network/local/netmask = 100.64.15.0/100.64.15.2/255.255.255.0 [SUCCEEDED]
Wed Jul 13 11:40:27 2022 Notified TAP-Windows driver to set a DHCP IP/netmask of 100.64.15.2/255.255.255.0 on interface {71102C25-61CA-464A-876F-EF2B06161508} [DHCP-serv: 100.64.15.0, lease-time: 31536000]
Wed Jul 13 11:40:27 2022 Successful ARP Flush on interface [37] {71102C25-61CA-464A-876F-EF2B06161508}
Wed Jul 13 11:40:27 2022 IPv4 MTU set to 1500 on interface 37 using service
Wed Jul 13 11:40:32 2022 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Wed Jul 13 11:40:32 2022 Initialization Sequence Completed