Доброго времени суток! Пытаюсь пробросить 80 порт во внутреннюю сет тика, но что то не выходит, в лог от НАТ правила получаю dstnat: in:COD-IP1 out:(unknown 0)
Помогите разобраться кого не затруднит
правила
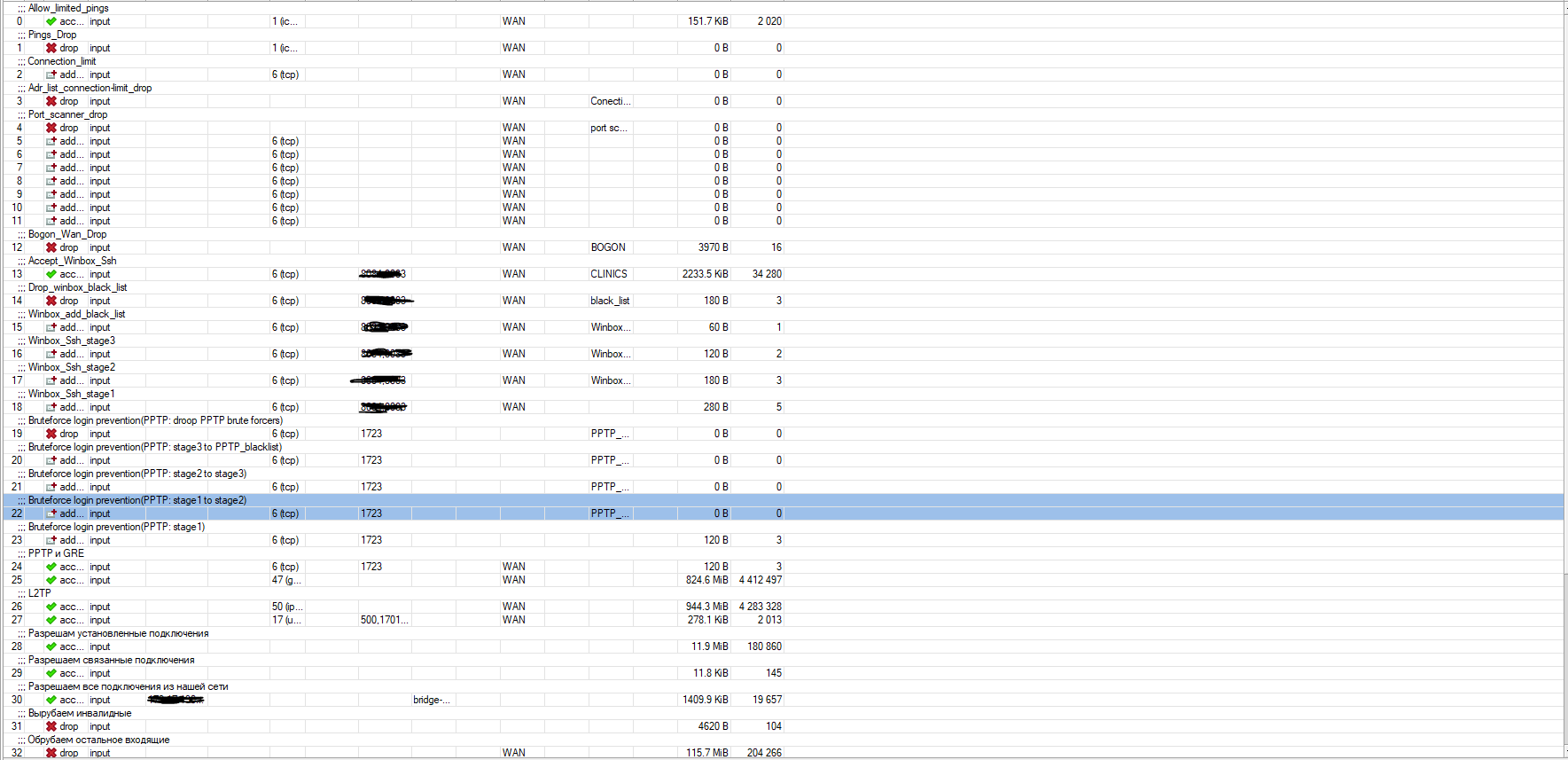

/ip firewall filter
add action=accept chain=input comment=Allow_limited_pings in-interface-list=WAN limit=50,5:packet protocol=icmp
add action=drop chain=input comment="Pings_Drop " in-interface-list=WAN protocol=icmp
add action=add-dst-to-address-list address-list=Conection-limit address-list-timeout=1d chain=input comment=Connection_limit connection-limit=200,32 in-interface-list=WAN protocol=tcp
add action=drop chain=input comment=Adr_list_connection-limit_drop in-interface-list=WAN src-address-list=Conection-limit
add action=drop chain=input comment=Port_scanner_drop in-interface-list=WAN src-address-list="port scanners"
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w chain=input in-interface-list=WAN protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=drop chain=input comment=Bogon_Wan_Drop in-interface-list=WAN src-address-list=BOGON
add action=accept chain=input comment=Accept_Winbox_Ssh dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp src-address-list=CLINICS
add action=drop chain=input comment=Drop_winbox_black_list dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp src-address-list=black_list
add action=add-src-to-address-list address-list=black_list address-list-timeout=5m chain=input comment=Winbox_add_black_list connection-state=new dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp src-address-list=Winbox_Ssh_stage3
add action=add-src-to-address-list address-list=Winbox_Ssh_stage3 address-list-timeout=1m chain=input comment=Winbox_Ssh_stage3 connection-state=new dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp src-address-list=Winbox_Ssh_stage2
add action=add-src-to-address-list address-list=Winbox_Ssh_stage2 address-list-timeout=1m chain=input comment=Winbox_Ssh_stage2 connection-state=new dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp src-address-list=Winbox_Ssh_stage1
add action=add-src-to-address-list address-list=Winbox_Ssh_stage1 address-list-timeout=1m chain=input comment=Winbox_Ssh_stage1 connection-state=new dst-port=WINBOXPORT,WEBPORT in-interface-list=WAN protocol=tcp
add action=drop chain=input comment="Bruteforce login prevention(PPTP: droop PPTP brute forcers)" dst-port=1723 protocol=tcp src-address-list=PPTP_blacklist
add action=add-src-to-address-list address-list=PPTP_blacklist address-list-timeout=2w1d chain=input comment="Bruteforce login prevention(PPTP: stage3 to PPTP_blacklist)" connection-state=new dst-port=1723 protocol=tcp src-address-list=PPTP_stage_3
add action=add-src-to-address-list address-list=PPTP_stage_3 address-list-timeout=1m chain=input comment="Bruteforce login prevention(PPTP: stage2 to stage3)" connection-state=new dst-port=1723 protocol=tcp src-address-list=PPTP_stage_2
add action=add-src-to-address-list address-list=PPTP_stage_2 address-list-timeout=6h chain=input comment="Bruteforce login prevention(PPTP: stage1 to stage2)" connection-state=new dst-port=1723 protocol=tcp src-address-list=PPTP_stage_1
add action=add-src-to-address-list address-list=PPTP_stage_1 address-list-timeout=12h chain=input comment="Bruteforce login prevention(PPTP: stage1)" connection-state=new dst-port=1723 protocol=tcp
add action=accept chain=input comment="PPTP \E8 GRE" dst-port=1723 in-interface-list=WAN protocol=tcp
add action=accept chain=input in-interface-list=WAN protocol=gre
add action=accept chain=input comment=L2TP in-interface-list=WAN protocol=ipsec-esp
add action=accept chain=input dst-port=500,1701,4500 in-interface-list=WAN protocol=udp
add action=accept chain=input comment="\D0\E0\E7\F0\E5\F8\E0\EC \F3\F1\F2\E0\ED\EE\E2\EB\E5\ED\ED\FB\E5 \EF\EE\E4\EA\EB\FE\F7\E5\ED\E8\FF" connection-state=established
add action=accept chain=input comment="\D0\E0\E7\F0\E5\F8\E0\E5\EC \F1\E2\FF\E7\E0\ED\ED\FB\E5 \EF\EE\E4\EA\EB\FE\F7\E5\ED\E8\FF" connection-state=related
add action=accept chain=input comment="\D0\E0\E7\F0\E5\F8\E0\E5\EC \E2\F1\E5 \EF\EE\E4\EA\EB\FE\F7\E5\ED\E8\FF \E8\E7 \ED\E0\F8\E5\E9 \F1\E5\F2\E8" in-interface=bridge-COD src-address=LAN-ip/24
add action=drop chain=input comment="\C2\FB\F0\F3\E1\E0\E5\EC \E8\ED\E2\E0\EB\E8\E4\ED\FB\E5" connection-state=invalid disabled=yes
add action=drop chain=input comment="\CE\E1\F0\F3\E1\E0\E5\EC \EE\F1\F2\E0\EB\FC\ED\EE\E5 \E2\F5\EE\E4\FF\F9\E8\E5" disabled=yes in-interface-list=WAN log-prefix=dropINOTHER
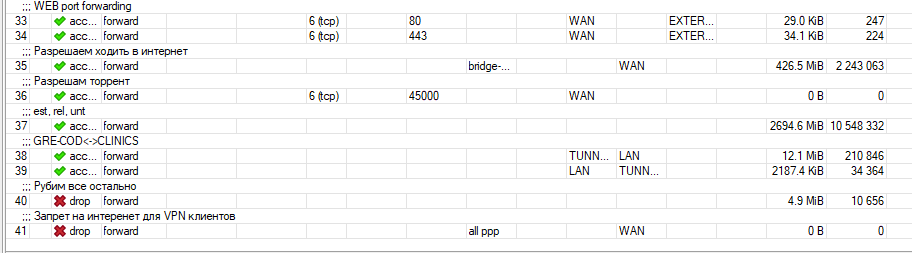
add action=drop chain=forward comment="\C7\E0\EF\F0\E5\F2 \ED\E0 \E8\ED\F2\E5\F0\E5\ED\E5\F2 \E4\EB\FF VPN \EA\EB\E8\E5\ED\F2\EE\E2" disabled=yes in-interface=all-ppp out-interface-list=WAN
add action=accept chain=forward comment="\D0\E0\E7\F0\E5\F8\E0\E5\EC \F5\EE\E4\E8\F2\FC \E2 \E8\ED\F2\E5\F0\ED\E5\F2" in-interface=bridge-COD out-interface-list=WAN
add action=accept chain=forward comment="\D0\E0\E7\F0\E5\F8\E0\EC \F2\EE\F0\F0\E5\ED\F2" dst-port=45000 in-interface-list=WAN protocol=tcp
add action=accept chain=forward comment="est, rel, unt" connection-state=established
add action=accept chain=forward comment=GRE-COD<->CLINICS in-interface-list=TUNNELS out-interface-list=LAN
add action=accept chain=forward in-interface-list=LAN out-interface-list=TUNNELS
add action=accept chain=forward dst-port=80 in-interface-list=WAN protocol=tcp src-address-list=EXTERNAL-WEB-ACCESS
add action=drop chain=forward comment="\D0\F3\E1\E8\EC \E2\F1\E5 \EE\F1\F2\E0\EB\FC\ED\EE" disabled=yes log-prefix=dropALL
add action=drop chain=forward connection-state=invalid disabled=yes log-prefix=dropfor
/ip firewall nat
add action=masquerade chain=srcnat out-interface-list=WAN
add action=masquerade chain=srcnat out-interface=all-ppp
add action=dst-nat chain=dstnat comment="WEB to 1c" dst-port=80 in-interface-list=WAN log=yes log-prefix=80web protocol=tcp src-address-list=EXTERNAL-WEB-ACCESS to-addresses=1С-srv-ip
add action=dst-nat chain=dstnat dst-port=443 in-interface-list=WAN log=yes log-prefix=443web protocol=tcp src-address-list=EXTERNAL-WEB-ACCESS to-addresses=1С-srv-ip
/ip firewall raw
add action=notrack chain=prerouting protocol=gre


