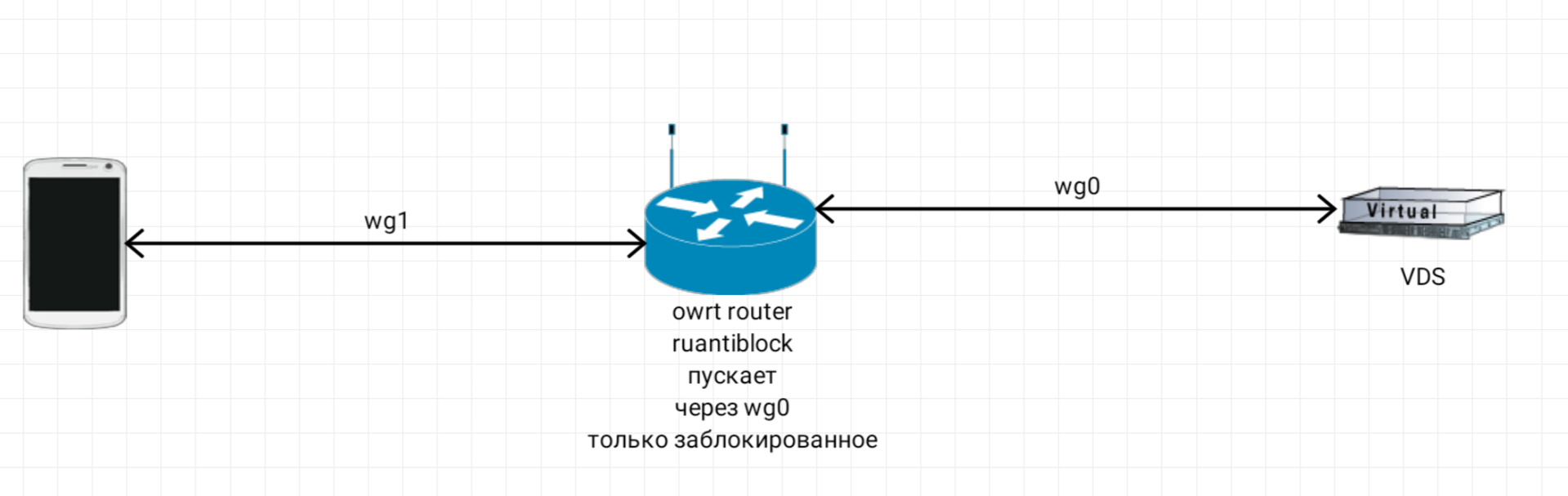
#
*nat
:PREROUTING ACCEPT [1432:282333]
:INPUT ACCEPT [386:25931]
:OUTPUT ACCEPT [442:29731]
:POSTROUTING ACCEPT [28:2016]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:postrouting_wg0_rule - [0:0]
:postrouting_wg1_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:prerouting_wg0_rule - [0:0]
:prerouting_wg1_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
:zone_wg0_postrouting - [0:0]
:zone_wg0_prerouting - [0:0]
:zone_wg1_postrouting - [0:0]
:zone_wg1_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wan -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i wg0 -m comment --comment "!fw3" -j zone_wg0_prerouting
-A PREROUTING -i wg1 -m comment --comment "!fw3" -j zone_wg1_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wan -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o wg0 -m comment --comment "!fw3" -j zone_wg0_postrouting
-A POSTROUTING -o wg1 -m comment --comment "!fw3" -j zone_wg1_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
-A zone_wg0_postrouting -m comment --comment "!fw3: Custom wg0 postrouting rule chain" -j postrouting_wg0_rule
-A zone_wg0_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wg0_prerouting -m comment --comment "!fw3: Custom wg0 prerouting rule chain" -j prerouting_wg0_rule
-A zone_wg1_postrouting -m comment --comment "!fw3: Custom wg1 postrouting rule chain" -j postrouting_wg1_rule
-A zone_wg1_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wg1_prerouting -m comment --comment "!fw3: Custom wg1 prerouting rule chain" -j prerouting_wg1_rule*mangle
:PREROUTING ACCEPT [1083788:1450688590]
:INPUT ACCEPT [502544:728329903]
:FORWARD ACCEPT [580860:722242893]
:OUTPUT ACCEPT [235920:30861615]
:POSTROUTING ACCEPT [816534:753092172]
:ruantiblock_action - [0:0]
:ruantiblock_allowed_hosts - [0:0]
:ruantiblock_blacklist - [0:0]
-A PREROUTING -j ruantiblock_allowed_hosts
-A FORWARD -o wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o wg0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wg0 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i wg0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wg0 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A OUTPUT -j ruantiblock_blacklist
-A ruantiblock_action -j MARK --set-xmark 0x8/0xffffffff
-A ruantiblock_allowed_hosts -j ruantiblock_blacklist
-A ruantiblock_blacklist -m set --match-set rc dst -j ruantiblock_action
-A ruantiblock_blacklist -m set --match-set ri dst -j ruantiblock_action
-A ruantiblock_blacklist -m set --match-set rd dst -j ruantiblock_action*filter
:INPUT ACCEPT [14:1177]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:forwarding_wg0_rule - [0:0]
:forwarding_wg1_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:input_wg0_rule - [0:0]
:input_wg1_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:output_wg0_rule - [0:0]
:output_wg1_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
:zone_wg0_dest_ACCEPT - [0:0]
:zone_wg0_dest_REJECT - [0:0]
:zone_wg0_forward - [0:0]
:zone_wg0_input - [0:0]
:zone_wg0_output - [0:0]
:zone_wg0_src_ACCEPT - [0:0]
:zone_wg1_dest_ACCEPT - [0:0]
root@OpenWrt:~# iptables-save -t mangleiptables-save -t mangleiptables-save -t mangle
:zone_wg1_input - [0:0]
:zone_wg1_output - [0:0]
:zone_wg1_src_ACCEPT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wan -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i wg0 -m comment --comment "!fw3" -j zone_wg0_input
-A INPUT -i wg1 -m comment --comment "!fw3" -j zone_wg1_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wan -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i wg0 -m comment --comment "!fw3" -j zone_wg0_forward
-A FORWARD -i wg1 -m comment --comment "!fw3" -j zone_wg1_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wan -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o wg0 -m comment --comment "!fw3" -j zone_wg0_output
-A OUTPUT -o wg1 -m comment --comment "!fw3" -j zone_wg1_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wg0 forwarding policy" -j zone_wg0_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wan -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wan -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -p udp -m udp --dport 51840 -m comment --comment "!fw3: Allow-wg1" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wan -m comment --comment "!fw3" -j reject
-A zone_wg0_dest_ACCEPT -o wg0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wg0_dest_ACCEPT -o wg0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wg0_dest_REJECT -o wg0 -m comment --comment "!fw3" -j reject
-A zone_wg0_forward -m comment --comment "!fw3: Custom wg0 forwarding rule chain" -j forwarding_wg0_rule
-A zone_wg0_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wg0_forward -m comment --comment "!fw3" -j zone_wg0_dest_REJECT
-A zone_wg0_input -m comment --comment "!fw3: Custom wg0 input rule chain" -j input_wg0_rule
-A zone_wg0_input -p tcp -m tcp --sport 13069 --dport 13069 -m comment --comment "!fw3: SSH" -j ACCEPT
-A zone_wg0_input -p udp -m udp --sport 13069 --dport 13069 -m comment --comment "!fw3: SSH" -j ACCEPT
-A zone_wg0_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wg0_input -m comment --comment "!fw3" -j zone_wg0_src_ACCEPT
-A zone_wg0_output -m comment --comment "!fw3: Custom wg0 output rule chain" -j output_wg0_rule
-A zone_wg0_output -m comment --comment "!fw3" -j zone_wg0_dest_ACCEPT
-A zone_wg0_src_ACCEPT -i wg0 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wg1_dest_ACCEPT -o wg1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wg1_dest_ACCEPT -o wg1 -m comment --comment "!fw3" -j ACCEPT
-A zone_wg1_forward -m comment --comment "!fw3: Custom wg1 forwarding rule chain" -j forwarding_wg1_rule
-A zone_wg1_forward -m comment --comment "!fw3: Zone wg1 to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_wg1_forward -m comment --comment "!fw3: Zone wg1 to wg0 forwarding policy" -j zone_wg0_dest_ACCEPT
-A zone_wg1_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wg1_forward -m comment --comment "!fw3" -j zone_wg1_dest_ACCEPT
-A zone_wg1_input -m comment --comment "!fw3: Custom wg1 input rule chain" -j input_wg1_rule
-A zone_wg1_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wg1_input -m comment --comment "!fw3" -j zone_wg1_src_ACCEPT
-A zone_wg1_output -m comment --comment "!fw3: Custom wg1 output rule chain" -j output_wg1_rule
-A zone_wg1_output -m comment --comment "!fw3" -j zone_wg1_dest_ACCEPT
-A zone_wg1_src_ACCEPT -i wg1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPTIptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -i wg1 -j MARK --set-mark $VPN_PKTS_MARKIP_CMD="ip"
IPT_CMD=`which iptables-legacy`
if [ $? -ne 0 ]; then
IPT_CMD=`which iptables`
if [ $? -ne 0 ]; then
echo " Error! Iptables doesn't exists" >&2
exit 1
fi
fi
IPT_ALLOWED_HOSTS_CHAIN="${NAME}_allowed_hosts"
IPT_BLLIST_CHAIN="${NAME}_blacklist"
IPT_ACTION_CHAIN="${NAME}_action"
IPT_FIRST_CHAIN="PREROUTING"
VPN_ROUTE_TABLE_ID=99
case "$ALLOWED_HOSTS_MODE" in
"1")
IPT_ALLOWED_HOSTS_RULE="-m set --match-set ${IPSET_ALLOWED_HOSTS} src -j ${IPT_BLLIST_CHAIN}"
;;
"2")
IPT_ALLOWED_HOSTS_RULE="-m set ! --match-set ${IPSET_ALLOWED_HOSTS} src -j ${IPT_BLLIST_CHAIN}"
;;
*)
IPT_ALLOWED_HOSTS_RULE="-j ${IPT_BLLIST_CHAIN}"
;;
esac
if [ "$PROXY_MODE" = "2" ]; then
IPT_TABLE="mangle"
else
IPT_TABLE="nat"
fi
IptCmdWrapper() {
local _i=0 _attempts=10 _return_code=1
while [ $_i -lt $_attempts ]
do
if $*; then
_return_code=$?
break
fi
_i=`expr $_i + 1`
done
return $_return_code
}
IptVpnRouteAdd() {
VPN_IP=`$IP_CMD addr list dev $IF_VPN 2> /dev/null | $AWK_CMD '/inet/{sub("/[0-9]{1,2}$", "", $2); print $2; exit}'`
if [ -n "$VPN_IP" ]; then
echo 0 > /proc/sys/net/ipv4/conf/$IF_VPN/rp_filter
IptVpnRouteDel 2> /dev/null
$IP_CMD rule add fwmark $VPN_PKTS_MARK table $VPN_ROUTE_TABLE_ID priority 1000
$IP_CMD route add default via $VPN_IP table $VPN_ROUTE_TABLE_ID
fi
}
IptVpnRouteDel() {
$IP_CMD route flush table $VPN_ROUTE_TABLE_ID
$IP_CMD rule del table $VPN_ROUTE_TABLE_ID
}
IptVpnRouteStatus() {
[ -n "`$IP_CMD route show table $VPN_ROUTE_TABLE_ID 2> /dev/null`" ] && return 0
return 1
}
IptMainAdd() {
local _set
$IPT_CMD -t "$IPT_TABLE" -N "$IPT_ACTION_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -N "$IPT_BLLIST_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -N "$IPT_ALLOWED_HOSTS_CHAIN"
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ALLOWED_HOSTS_CHAIN" $IPT_ALLOWED_HOSTS_RULE
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -I "$IPT_FIRST_CHAIN" 1 -j "$IPT_ALLOWED_HOSTS_CHAIN"
if [ "$PROXY_MODE" = "2" ]; then
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -j MARK --set-mark $VPN_PKTS_MARK
#добавлено для wg1 ########################################################################
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -i wg1 -j MARK --set-mark $VPN_PKTS_MARK
#добавлено для wg1 ########################################################################
IPT_IPSETS="${IPSET_CIDR} ${IPSET_IP} ${IPSET_DNSMASQ}"
else
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -p tcp -j REDIRECT --to-ports ${TOR_TRANS_PORT}
if [ "$TOR_ALLOW_UDP" = "1" ]; then
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -p udp -j REDIRECT --to-ports ${TOR_TRANS_PORT}
fi
IPT_IPSETS="${IPSET_ONION} ${IPSET_CIDR} ${IPSET_IP} ${IPSET_DNSMASQ}"
fi
for _set in $IPT_IPSETS
do
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_BLLIST_CHAIN" -m set --match-set "$_set" dst -j "$IPT_ACTION_CHAIN"
done
if [ "$PROXY_MODE" = "2" ]; then
IptVpnRouteAdd
fi
}
IptMainDel() {
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -D "$IPT_FIRST_CHAIN" -j "$IPT_ALLOWED_HOSTS_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -F "$IPT_ALLOWED_HOSTS_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -X "$IPT_ALLOWED_HOSTS_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -F "$IPT_BLLIST_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -X "$IPT_BLLIST_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -F "$IPT_ACTION_CHAIN"
$IPT_CMD -t "$IPT_TABLE" -X "$IPT_ACTION_CHAIN"
if [ "$PROXY_MODE" = "2" ]; then
IptVpnRouteDel 2> /dev/null
fi
}
IPT_OUTPUT_FIRST_RULE="-j ${IPT_BLLIST_CHAIN}"
IptLocalClientsAdd() {
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -I OUTPUT 1 $IPT_OUTPUT_FIRST_RULE
}
IptLocalClientsDel() {
IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -D OUTPUT $IPT_OUTPUT_FIRST_RULE
}
IptListBllistChain() {
$IPT_CMD -t "$IPT_TABLE" -v -L "$IPT_BLLIST_CHAIN"
}IptCmdWrapper $IPT_CMD -t "$IPT_TABLE" -A "$IPT_ACTION_CHAIN" -i wg1 -j MARK --set-mark $VPN_PKTS_MARKconfig redirect
option src 'lan'
option src_dport '53'
option target 'DNAT'
option dest_ip '192.168.0.1'
option name 'dnsproxy-dns-leaks'
config redirect
option src 'wg1'
option src_dport '53'
option target 'DNAT'
option dest_ip '192.168.0.1'
option name 'dnsproxy-dns-leaks_wg1'
config redirect
option src 'wg1'
option src_dport '853'
option target 'DNAT'
option dest_ip '192.168.0.1'
option name 'dnsproxy-dns-leaks_wg1-2'