
Linux
1
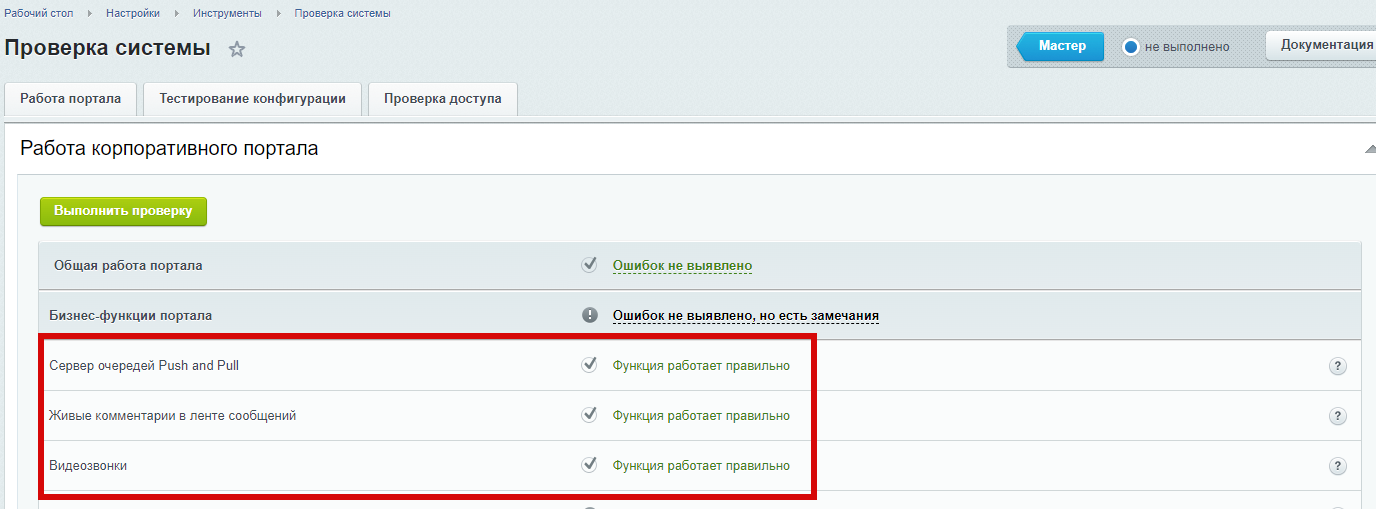
Вклад в тег
pvcreate --uuid "тут UUID того PV который [unknown]" --restorefile /etc/lvm/archive/{тут файл архива .vg который бал на момент изначального расширения +20Гб моей VG} /dev/sdb2vgcfgrestore vg1vgextend /dev/sdb2 vg1
vgcfgrestore -f /etc/lvm/archive/{тут файл архива .vg который бал на момент изначального расширения +20Гб моей VG} vg1systemctl daemon-reload
partprobe/dev/mapper/vg1-lv1 118G 87G 26G 77% /home/bitrix/www/uploadpvdisplay
File descriptor 7 (pipe:[27112]) leaked on pvdisplay invocation. Parent PID 8769: bash
--- Physical volume ---
PV Name /dev/sdb1
VG Name vg1
PV Size <100.00 GiB / not usable 2.00 MiB
Allocatable yes (but full)
PE Size 4.00 MiB
Total PE 25599
Free PE 0
Allocated PE 25599
PV UUID sjXlXa-Ma5C-BT14-n0Na-69VR-BGzK-eIo7DW
--- Physical volume ---
PV Name /dev/sdb2
VG Name vg1
PV Size 20.00 GiB / not usable 4.00 MiB
Allocatable yes (but full)
PE Size 4.00 MiB
Total PE 5119
Free PE 0
Allocated PE 5119
PV UUID vBNMOq-iIQD-0H1B-nosS-iWmt-wzKm-IMslD6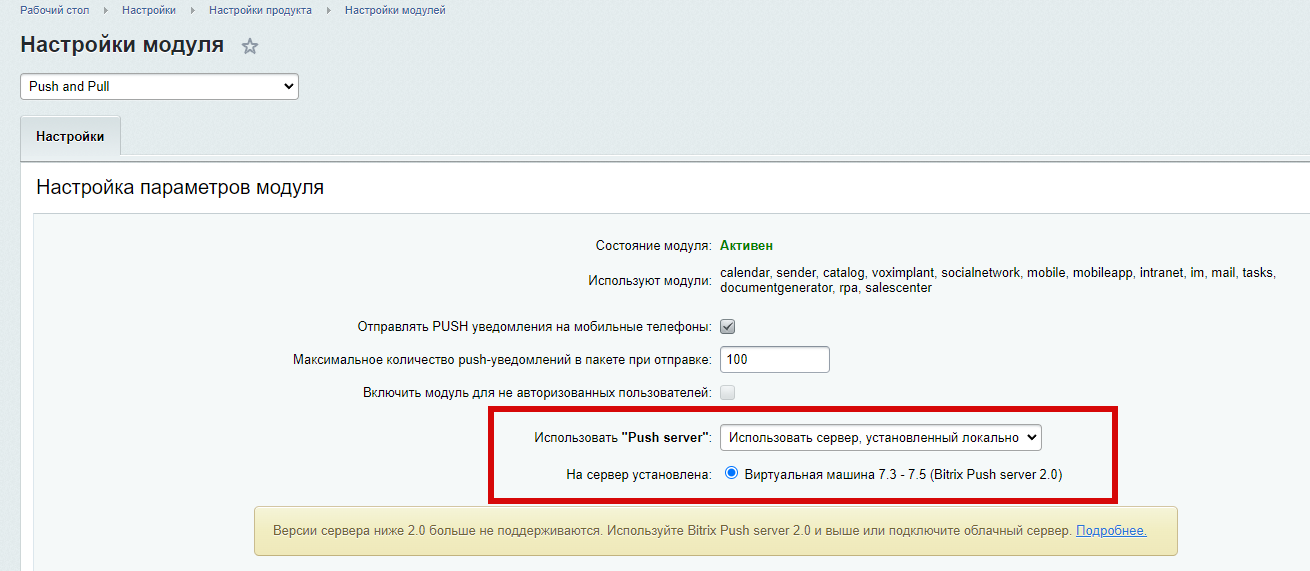
iptables -I INPUT -p tcp --match multiport --dport 8010:8015 -j ACCEPT
iptables -I INPUT -p tcp --match multiport --dport 9010:9011 -j ACCEPTnetstat -ntulpupstream nodejs_sub {
ip_hash;
keepalive 1024;
server push:8010;
server push:8011;
server push:8012;
server push:8013;
server push:8014;
server push:8015;
}
upstream nodejs_pub {
ip_hash;
keepalive 1024;
server push:9010;
server push:9011;
}location ~* ^/bitrix/subws/ {
access_log off;
proxy_pass http://nodejs_sub;
...proxy_set_header Authorization "" ;include bx/settings/rtc-im_settings.conf;
include bx/bx_general_proxy_settings.conf;proxy_connect_timeout 300;
proxy_send_timeout 300;
proxy_read_timeout 300;
proxy_buffer_size 64k;
proxy_buffers 8 256k;
proxy_busy_buffers_size 256k;
proxy_temp_file_write_size 10m;
gzip on;
gzip_proxied any;
gzip_static on;
gzip_http_version 1.0;
gzip_types application/x-javascript application/javascript text/css;
default_type application/force-download;
tcp_nopush on;
tcp_nodelay on;
client_max_body_size 1024m;
client_body_buffer_size 4m;log_format simple '$time_local $status $request';
# if connection ti not set
map $http_upgrade $connection_upgrade {
default upgrade;
'' 'close';
}
map $http_upgrade $replace_upgrade {
default $http_upgrade;
'' "websocket";server {
listen 80;
if ($host = {DNS name}) {
return 301 https://$host$request_uri;
} # managed by Certbot
}
server {
listen 443 ssl;
server_name {DNS name} www.{DNS name};
access_log /var/www/httpd-logs/{DNS name}.access.log;
error_log /var/www/httpd-logs/{DNS name}.error.log notice;
ssl_certificate /etc/letsencrypt/live/{DNS name}/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/{DNS name}.su/privkey.pem; # managed by Certbot
ssl_ciphers EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH;
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
location / {
proxy_ignore_client_abort on;
proxy_pass https://{IP VM B24}:443;
proxy_redirect https://{IP VM B24}:443 /;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header HTTPS YES;
# for Push&Pull
location /bitrix/subws/ {
access_log off;
proxy_max_temp_file_size 0;
proxy_read_timeout 43800;
proxy_http_version 1.1;
proxy_pass https://{IP VM B24}:443;
proxy_set_header Upgrade $replace_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_redirect https://{IP VM B24}:443 /;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header HTTPS YES;
}
location /bitrix/sub/ {
access_log off;
rewrite ^/bitrix/sub/(.*)$ /bitrix/subws/$1 break;
proxy_pass https://{IP VM B24}:443;
proxy_max_temp_file_size 0;
proxy_read_timeout 43800;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header HTTPS YES;
}
location /bitrix/rest/ {
access_log off;
proxy_pass https://{IP VM B24}:443;
proxy_max_temp_file_size 0;
proxy_read_timeout 43800;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header HTTPS YES;
}
}nginx -s reloadnginx -tsystemctl restart nginxset_real_ip_from {IP revers-proxy};
real_ip_header X-Forwarded-For;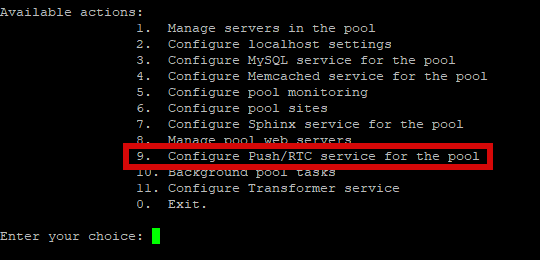
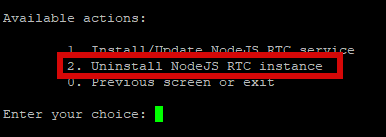
событие на получение почты onMailMessageNew
<?php
use Bitrix\Main\Diag\Debug;
use Bitrix\Mail\Helper\Message;
use \Bitrix\Main\Entity\Event;
CModule::IncludeModule('mail');
$eventManager = \Bitrix\Main\EventManager::getInstance();
$eventManager->addEventHandler('mail', 'onMailMessageNew', 'onMailMessageNew');
function onMailMessageNew($event)
{
$message = $event->getParameter('message');
Debug::dumpToFile( $message);
}/etc/hosts на backend серверах сопоставление доменов с frontend сервером (именно frontend!). Если при этом требуется, чтобы сервер мог обращаться ещё и сам к себе по некоторому доменному имени (это надо например push-server в Битрикс), то надо прописать любое выдуманное имя хоста в /etc/hostname, и отдельной записью прописать его на локальный IP в /etc/hosts--with-stream_ssl_module
--with-stream_ssl_preread_module
--with-stream_realip_moduleuser www-data;
worker_processes auto;
worker_rlimit_nofile 10240;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
use epoll;
worker_connections 30720;
multi_accept on;
}
stream {
proxy_protocol on; #обязательно включаем, без него IP адреса из приходящего SSL трафика не передать дальше
map $ssl_preread_server_name $name {
siteone.ru so;
sitetwo.ru st;
sitetree.ru str;
}
#bitrix1
upstream so80 {
server 192.168.0.100:80;
}
upstream so443 {
server 192.168.0.100:443;
}
upstream so8893 {
server 192.168.0.100:8893;
}
upstream so8894 {
server 192.168.0.100:8894;
}
#bitrix2
upstream st80 {
server 192.168.88.114:80;
}
upstream st443 {
server 192.168.88.114:443;
}
upstream st8893 {
server 192.168.88.114:8893;
}
upstream st8894 {
server 192.168.88.114:8894;
}
#web site
upstream str80 {
server 192.168.88.102:80;
}
upstream str443 {
server 192.168.88.102:443;
}
#web traffic
server {
listen 80;
proxy_pass ${name}80;
}
server {
listen 443;
proxy_pass ${name}443;
ssl_preread on;
}
#push&pull bitrix
server {
listen 8893;
proxy_pass ${name}8893;
}
server {
listen 8894;
proxy_pass ${name}8894;
ssl_preread on;
}
}listen дописываем proxy_protocol, иначе вообще не заработает.server {
listen 443 default_server ssl proxy_protocol;
...
proxy_set_header X-Real-IP $proxy_protocol_addr;
proxy_set_header X-Forwarded-For $proxy_protocol_addr;
...
}http http {
set_real_ip_from #IP вашего frontend#;
real_ip_header proxy_protocol;
}/etc/hosts как описано выше.