const Excel = require('exceljs');
(async()=>{
const workbook = new Excel.Workbook();
await workbook.xlsx.readFile("./template.xlsx");
await workbook.xlsx.writeFile("./test.xlsx");
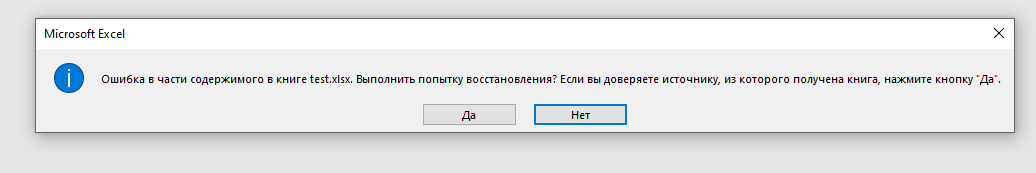
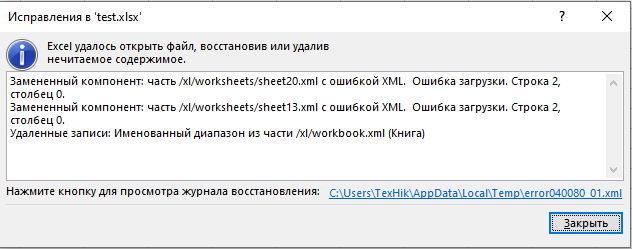
})();
#include <Windows.h>
#include <iostream>
using namespace std;
bool Inject(DWORD pId, char *dllName)
{
HANDLE h = OpenProcess(PROCESS_ALL_ACCESS, true, pId);
if (h)
{
LPVOID LoadLibAddr = (LPVOID)GetProcAddress(GetModuleHandleA("kernel32.dll"), "LoadLibraryA");
LPVOID dereercomp = VirtualAllocEx(h, NULL, strlen(dllName), MEM_COMMIT | MEM_RESERVE, PAGE_READWRITE);
WriteProcessMemory(h, dereercomp, dllName, strlen(dllName), NULL);
HANDLE asdc = CreateRemoteThread(h, NULL, NULL, (LPTHREAD_START_ROUTINE)LoadLibAddr, dereercomp, 0, NULL);
WaitForSingleObject(asdc, INFINITE);
VirtualFreeEx(h, dereercomp, strlen(dllName), MEM_RELEASE);
CloseHandle(asdc);
CloseHandle(h);
return true;
}
return false;
}
bool SetPrivilege(LPCWSTR lpszPrivilege, BOOL bEnablePrivilege) {
TOKEN_PRIVILEGES priv = { 0,0,0,0 };
HANDLE hToken = NULL;
LUID luid = { 0,0 };
if (!OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES, &hToken)) {
if (hToken)
CloseHandle(hToken);
return false;
}
if (!LookupPrivilegeValueW(0, lpszPrivilege, &luid)) {
if (hToken)
CloseHandle(hToken);
return false;
}
priv.PrivilegeCount = 1;
priv.Privileges[0].Luid = luid;
priv.Privileges[0].Attributes = bEnablePrivilege ? SE_PRIVILEGE_ENABLED : SE_PRIVILEGE_REMOVED;
if (!AdjustTokenPrivileges(hToken, false, &priv, 0, 0, 0)) {
if (hToken)
CloseHandle(hToken);
return false;
}
if (hToken)
CloseHandle(hToken);
return true;
}
void main() {
SetPrivilege(SE_DEBUG_NAME, TRUE);
DWORD pid;
cout << "Enter process id: ";
cin >> pid;
Inject(pid, "C:\\Users\\TexHik\\Documents\\Visual Studio 2017\\Projects\\Cheat\\Debug\\dll.dll");
system("pause");
}// dllmain.cpp: определяет точку входа для приложения DLL.
#include "stdafx.h"
#include <sstream>
void Hack()
{
MessageBox(NULL, L"Helllo!!!!!", NULL, NULL);
}
BOOL APIENTRY DllMain( HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved)
{
if (ul_reason_for_call == DLL_PROCESS_ATTACH) {
Hack();
}
}